 |
| Visitors bike past shops in downtown Tulum, Mexico
Nearly 70 million Americans traveled abroad last year. Even more people visited the U.S., continuing a trend that began about five years ago amid efforts to reverse a decline in tourism caused by the financial crisis and tighter security. In 2010, Congress created a body to promote tourism in the United States; two years later, the White House followed with an executive order (PDF) aimed at speeding visa approvals.
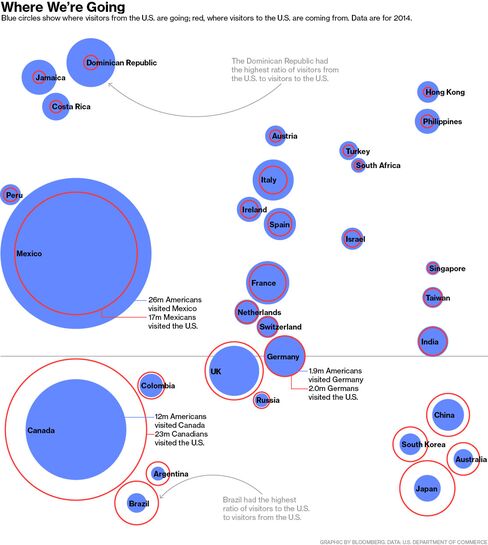
Where do Americans go? Canada and Mexico, of course. Excluding those two, 30.8 million Americans traveled abroad last year, led by Californians and New Yorkers, according to recent data (including both business and leisure travel) from the Commerce Department's National Travel and Tourism Office.
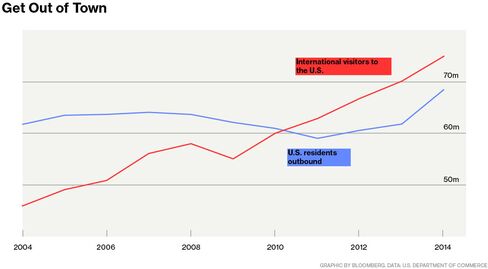
Canadians visit the U.S. more than Americans visit Canada. More than twice as many Americans visited Mexico in 2014 as headed north, those sunny beaches trumping the friendly nation of hockey, poutine, and Justin Bieber. Among overseas destinations, the United Kingdom and the Dominican Republic drew the most U.S. travelers, followed by France, Italy, and Germany.
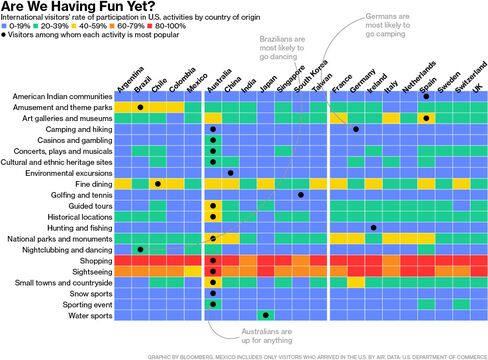
What do tourists do when they come to America? Everybody shops. But nobody enjoys golf and tennis like South Koreans. Chileans prefer U.S.-style fine dining, and Spanish travelers come for the art galleries and Native American cultural attractions. The outlier: Australians, who apparently don't go in for sleep.
 |
Thursday, August 13, 2015
The Great American Vacation in Three Charts (BusinessWeek)
Tuesday, August 11, 2015
Monday, August 10, 2015
Attackers can access Dropbox, Google Drive, OneDrive files without a user's password (CNet)
The so-called "man-in-the-cloud" attack is said to be a common flaw in most cloud-based file synchronization services.
 |
| ropbox is one of those affected by this cloud vulnerability (Image: CNET)
Hackers don't even need your password anymore to get access to your cloud data.
Newly published research, released at the Black Hat conference in Las Vegas on Wednesday by security firm Imperva, shows how a "man-in-the-cloud" attack can grab cloud-based files -- as well as infecting users with malware -- without users even noticing.
|
The attack differs from traditional man-in-the-middle attacks, which rely on tapping data in transit between two servers or users, because it exploits a vulnerability in the design of many file synchronization offerings, including Google, Box, Microsoft, and Dropbox services.
This is not just an issue for consumers, but also businesses, which increasingly use cloud-based services to share sensitive customer and corporate data.
The report by Imperva, which has a research unit as well as having a commercial stake in the security space, said in some cases "recovery of the account from this type of compromise is not always feasible."
The attack works by grabbing the password token, a small file that sits on a user's devices for convenience (which saves the user from entering their password each time). When the token is obtained, either through a phishing attack or a drive-by exploit, it can be used to fool a new machine into thinking the attacker is the account's owner. From there, the attacker can access and steal files, and even add malware or ransomware (which is on the rise) to the victim's cloud folder, which can be used for further attacks.
Making matters worse, account owners are almost powerless. Because the tokens are tied to the user's device, changing the account password would not lock out the attacker.
"We should be really worried about this," said Amichai Schulman, chief technology office at Imperva, speaking to ZDNet on the phone earlier this week. "Attackers are looking at methods of being less detectable. But the reality is that it's already happening."
Recent research pointed to a sophisticated Russian hacker group targeting the cloud with Hammertoss, malware which sifts through network traffic, looking for ways to pilfer files and documents. Imperva also cited a paper by security firm Blue Coat, which showed a similar attack method in the wild.
But coming to the defense of the cloud providers, Schulman was somewhat hesitant to call the vulnerability a flat-out "design flaw."
"These services are meant to deliver files seamlessly from your computer to the cloud to other devices around the world. These services aren't dangerous or insecure," he added.
"It's kind of a trade-off between usability and security. It's just the way things work," he said.
"There isn't a simple fix," he said. Although many services now offer two-factor authentication and notifications when unauthorized access is detected -- such as from a new computer or an entirely different geography -- Schulman said many people either ignore those notifications or choose not to do anything about them.
Dropbox declined to comment on the record. Google did not return an email requesting comment.
Friday, August 7, 2015
Islamic State Circulates Sex Slave Price List (BusinessWeek)

A senior United Nations official says Islamic State is circulating a slave price list for captured women and children, and that the group’s ongoing appeal and barbarity pose an unprecedented challenge.
The official, Zainab Bangura, said that on a trip to Iraq in April she was given a copy of an Islamic State pamphlet, which included the list, showing that captured children as young as one fetch the highest price. The bidders include both the group’s own fighters and wealthy Middle Easterners.
The list shows the group’s view of the value of those it captures and surfaced some eight months ago, though its authenticity came under question. Bangura, who is the UN special envoy on sexual violence in conflict and was also in Jordan and Turkey, said she has verified that the document came from Islamic State and reflects real transactions.
“The girls get peddled like barrels of petrol,” she said in an interview last week in New York. “One girl can be sold and bought by five or six different men. Sometimes these fighters sell the girls back to their families for thousands of dollars of ransom.”
For Islamic State fighters, the prices in Iraqi dinars for boys and girls aged 1 to 9 are equal to about $165, Bangura said. Prices for adolescent girls are $124 and it’s less for women over 20.
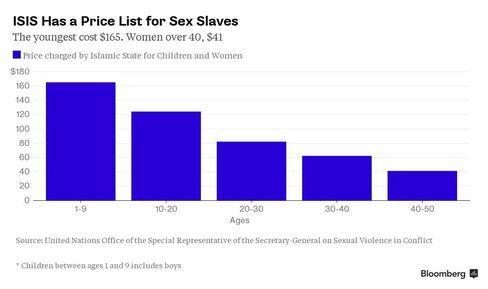
The militia’s leaders first take those they wish, after which rich outsiders from the region are permitted to bid thousands of dollars, Bangura said. Those remaining are then offered to the group’s fighters for the listed prices.
Verified List
Bangura, a Muslim and former foreign minister of Sierra Leone, said that Islamic State, which rules some 80,000 square miles across swathes of Iraq and Syria, is unlike other insurgent groups and challenges all known models of fighting them.
“It’s not an ordinary rebel group,” she said. “When you dismiss them as such, then you are using the tools you are used to. This is different. They have the combination of a conventional military and a well-run organized state.”
Officials and scholars have struggled to understand Islamic State’s success despite breaking what are widely seen as rules for insurgents -- to be sure to mingle with local populations, not take on established militaries or try to hold territory. The group has broken all those rules and draws thousands of foreign fighters despite its well-publicized savagery.
Below is a scanned copy of the list obtained and verified by the UN

Spread Fear
Kerry Crawford, who teaches at James Madison University in Harrisonburg, Virginia, said that publicizing the violations is used to the group’s advantage by building internal ties and external fear.
“If you and your group are doing something that is considered taboo, your doing it together forms a bond,” she said. “Sexual violence does really create fear within a population.”
She also said that sexual abuse by soldiers has a long history including the so-called rape camps in the former Yugoslavia in the 1990s.
Islamic State has made a particular practice of enslaving communities it has conquered that are not Sunni Muslim -- Yazidis and Christians, for example.
It portrays such conquests as God’s work, drawing disaffected Muslims from around the world.
Bangura said the international community and the UN have been taken aback by such practices because they do not resemble those of village militias in other countries.
“They have a machinery, they have a program,” she said. “They have a manual on how you treat these women. They have a marriage bureau which organizes all of these ‘marriages’ and the sale of women. They have a price list.”
Thursday, August 6, 2015
FBI:Public Service Announcement (I-073115-PSA)
Alert Number

July 31, 2015
Alert Number
I-073115-PSA
E-MAIL EXTORTION CAMPAIGNS THREATENING DISTRIBUTED DENIAL OF SERVICE ATTACKS
The Internet Crime Complaint Center (IC3) recently received an increasing number of complaints from businesses reporting extortion campaigns via e-mail. In a typical complaint, the victim business receives an e-mail threatening a Distributed Denial of Service (DDoS) attack to its Website unless it pays a ransom. Ransoms vary in price and are usually demanded in Bitcoin.
Victims that do not pay the ransom receive a subsequent threatening e-mail claiming that the ransom will significantly increase if the victim fails to pay within the time frame given. Some businesses reported implementing DDoS mitigation services as a precaution.
Businesses that experienced a DDoS attack reported the attacks consisted primarily of Simple Discovery Protocol (SSDP) and Network Time Protocol (NTP) reflection/amplification attacks, with an occasional SYN-flood and, more recently, Wordpress XML-RPC reflection/amplification attack. The attacks typically lasted one to two hours, with 30 to 35 gigabytes as the physical limit.
Based on information received at the IC3, the FBI suspects multiple individuals are involved in these extortion campaigns. The attacks are likely to expand to online industries and other targeted sectors, especially those susceptible to suffering financial losses if taken offline.
If you believe you have been a victim of this scam, you should reach out to your local FBI field office, and file a complaint with the IC3 at www.IC3.gov. Please provide any relevant information in your complaint, including the extortion e-mail with header information.
TIPS TO PROTECT YOURSELF:
- Do not open e-mail or attachments from unknown individuals.
- Do not communicate with the subject.
- If an attack occurs, utilize DDoS mitigation services.
Tuesday, August 4, 2015
Monday, August 3, 2015
Will artificial intelligence take over IT and the world? A Survey
Artificial intelligence (AI) has been a staple of sci-fi for decades. But it has a growing role in technology. Take this survey and tell us your thoughts on the current and future impact of AI.


Artificial intelligence (AI) has been a staple of science fiction and cinema for decades now, with one of the most famous early examples being Stanley Kubrick's film "2001: A Space Odyssey." It represented the potential - and the possible malice - of AI.
Of course, we can't talk about AI without pointing out that the theme of malice was carried on by such franchises as the Terminator series, in which an AI mechanism called Skynet decided mankind needed elimination and proceeded to attempt the execution thereof. As is Hollywood's wont, this is an extreme example, but there's no doubt that alongside the benefits AI is also seen as a possible threat to humans by taking away their thinking skills, decision-making capabilities and occupations (or very lives.)
Fiction aside, AI has been playing a genuine and beneficial role in technology, ever since IBM's Deep Blue computer, the precursor to their Watson cognitive framework, defeated chess wizard Garry Kasparov. We're now seeing AI in day-to-day interactions with Siri, Apple's personal assistant, which provides information in response to voice commands. It's present in phone systems which listen for human input then route calls accordingly. Aviation relies on it for airport gate selection and simulation strategies. Financial organizations use it to maintain operations, investments and properties. Toy makers have released electronic pets and robots with simple AI capabilities. You can even find AI in space probes which go where humans cannot and make calculations as needed based on programming instructions.
As AI advances, it's become apparent that there are some things machines are better at doing than humans, but humans still have plenty going for them (AI still doesn't possess the deep-thinking skills or planning capacity which can replace experienced workers in complex fields). We're interested in looking at how the two species are going to work in concert to deliver a more powerful future for IT, and the human race, and we have developed this AI survey as a result.
Please share your experiences, observations and views on the subject of AI and how it applies to your organization and career. Respondents will receive a free copy of the resulting research report.
Subscribe to:
Posts (Atom)


